With the growing digital disruption, DevOps has become the mainstream focus of various enterprises. But the move to digitization has widened the assault surface substantially that has resulted in highly expensive security breaches. Bearing this in mind, it is high time for organizations to evolve their DevOps into DevSecOps, with security baked into each and every stage of the software delivery cycle.
For the ease of understanding, let us think of a scenario where car manufacturers just focus on manufacturing cars without considering security. Would it help to focus on security after the car had been designed and assembled? I guess it would be too late by then. Now try applying the same analogy for a DevOps Ecosystem. It is important to focus on security in the first place, i.e. the planning and development phase. It is all about embracing the culture seeding security right in the beginning of SDLC. And to understand this better, let’s ponder on the different phases of SDLC below- –
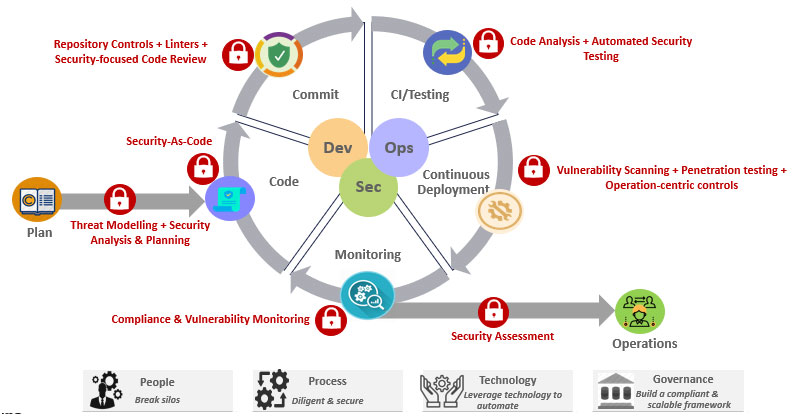
- PLAN: Mostly, in order to achieve quick time-to-market, security is taken as an afterthought which poses a great risk to the security of the application or product. Hence security planning & analysis holds a crucial place in the planning phase and can be implemented using the following hacks-
- Security Analysis & Planning: A proper security analysis should be done aligned with the goals & objectives. Depending on the complexity of business or an entity’s size, one or more security plans with their strategy, risk tolerance, checkpoints, risk mitigation plan and governance measures.
- Threat Modelling: This could be a 5-step approach of ‘Define ->Simulate -> Identify -> Mitigate -> Validate’ can be implemented using various threat modelling methodologies like STRIDE, PASTA, TRIKE, VAST,etc. Additionally, various threat modelling tools are available in the market like Microsoft Threat Modelling tool, Infection Monkey, SecuriCAD, etc. that conduct attack simulations on virtual models of collected data without impacting the actual environment, and then help us to visualize the environment with the possible threats and empower us to take preventive measures for them. It helps in identifying the areas which are more vulnerable to an attack.
- CODE: ‘Security-As-Code’ principle must be incorporated in the development phase by implementing secure coding best practices like cross browser security, controlled access to application or product, avoid complex architecture, reuse trusted components, etc.
- COMMIT: Along with good coding habits, a proper commit strategy is also needed as it acts as a crucial means of communication between the team members. It can be accomplished by implementing the following measures-
- Repository Controls & Linting: Educate & ensure security focussed IDE controls with proper lint checks to flag programming errors, bugs, stylistic errors and suspicious constructs. Also, proper security policies (for example, security.xml in git) & procedures must be in place to safeguard your code effectively.
- Security-focussed Reviews: Security is cumulative, i.e. composition of secure components result in secure application or product. Hence to ensure this, thorough security-focussed code reviews using review guides and checklists must be implemented. Monitoring the coding pattern to identify & track insecure code patterns also plays a key role in this phase.
- CONTINOUS INTEGRATION (CI) &CONTINOUS TESTING (CT): Automated pipelines inclusive of automated testing with proper security in terms of governance & compliance could be your “happily everafter” if implemented correctly. This can be achieved by-
- Code Analysis in CI: To ensure that your code adheres to the coding standards, code analysis using tools like SonarQube can be included in your CI pipelines with proper code quality gates. When it comes to creating pipelines, people tend to mix and match multiple tools or plugins for the various tasks performed in a pipeline. While doing so, you forget the fact open-source tools can eavesdrop your code. And so, choose and govern your open-source tool stack mindfully.
- Continuous Testing (CT):Despite the enticement of DevOps, a good velocity with timely delivery with greater quality is also important and hence this calls for a successful testing for stable and secure environments. White-box testing using SAST methodology and Black-box testing using DAST methodology must be implemented to identify security vulnerabilities that can make applications or products susceptible to attacks. All the stakeholders including QA, operations and developers must set a benchmark for testing matching the industry standards like OWASP.
- CONTINUS DEPLOYMENT (CD):Once CI is in place, CD simply takes ahead the integrated code to be released in the environment with the below key practices-
- Vulnerability Scan & Penetration Tests: Both of these tests aim at optimal network and application security. Vulnerability scans using tools are like quick X-rays that finds, reports and fixes the potential exposures, whereas Penetration Tests are like detailed MRI done by a professional manually to meticulously examine every nook and canny of the application and network using proper checklists and reports.
- Operation-centric controls: Once the code is deployed to the environment, it is important to have centralized visibility and controls like logging, event-monitoring, privilege management, etc. Additionally, it is important to safeguard your docker infrastructure by secure component analysis of docker images, identifying secrets and docker benchmark scanning. Also, if there are cloud-hosted environments, then security must be enforced for providers and consumers of cloud services. Cloud providers must ensure a secure infrastructure by implementing certain controls that are – i) preventive (against incidents), ii) deterrent (by warning the attackers), iii) detective (against potential threats and addressing them accordingly) and iv) corrective (remedial measures to limit the threats).
- MONITORING: An effective and continuous monitoring strategy helps you to gain insights about the health of your deployments and application and proactively limiting the threats by taking appropriate actions in response to them. A well-monitored ecosystem in the world of DevOps can be achieved by-
-
- Compliance & Vulnerability Monitoring: It is crucial to scan your ecosystem, evaluate your security levels and remediate the potential risks or threats. Hence harnessing the various monitoring tools to monitor your logging, compliance, vulnerabilities, dependency monitoring, etc. can act as saviours for your application or product.Additionally, it is crucial to scan your custom-built containers so that you can be sure they are not tampered with between build and deployment using opensource tools or customized wrappers.
- Security Assessment: Regular security assessment mechanisms must be in place that provide a snapshot of the current security standard of your ecosystem versus the security benchmarks in the industry. Running security audits using checklists, pondering over the generated security reports and then working on fixing the loopholes in them should be a shared responsibility of all the stakeholders including developers, QA and operations teams.
-
Conclusion:
Though DevOps has invigorated many enterprises to faster time-to-market with proofs of success in their pockets, but people generally tend to give security an afterthought. And these are later realized in highly expensive security breaches. Because not all villains wear masks, so you never know which ‘hole-in-the-wall’ of your ecosystem can invade your DevOps ecosystem. Agreed that no system can be 100% secure, but as “prevention is better than cure”, so it is always better to be armed with best security hacks to nip the evil (read threats) in the buds!












