This article is about what we learned from the failures of companies to stay on top of Data Privacy and Security and how they responded. It’s not about the failure of simply any company, but the good companies- the kinds that many managers have admired and tried to emulate.
Some of them took Data Privacy and Security more seriously than before after security-related incidents. They learned to build short- and long-term plans for better security. The basic core components for Data Privacy and Security can then be applied to new use cases and platforms when a new need arises.
Some of them learned before they experienced any major security incident from other companies in their industry how to implement best practices with granular Data Privacy and Security to achieve a defendable security posture. They assumed that an attacker might soon target their business or already be in their systems.
The security landscape is increasingly changing and needs to be monitored to stay vigilant. We’ve helped many clients build data privacy and security into their core business systems throughout the years.
Surprisingly, our discoveries have little to do with technical tools. But it has everything to do with how you communicate to find the balance between privacy, security, and compliance that is right for your Business. We have found that many of life’s most useful insights are often quite simple. Good security is also based on simple approaches.
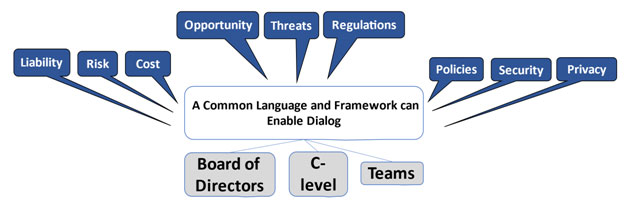
A Common Language and Framework can Enable Dialog
A Common Language can be based on a Risk Management Framework that can communicate in a common language that is understandable for the different teams that are involved:
Finding the Right Balance
A Common Language can Enable the Dialog for Finding the Right Balance between the two sides:
- Risks with Breaches and compliance to Regulations.
- Finding new and Business Opportunities.
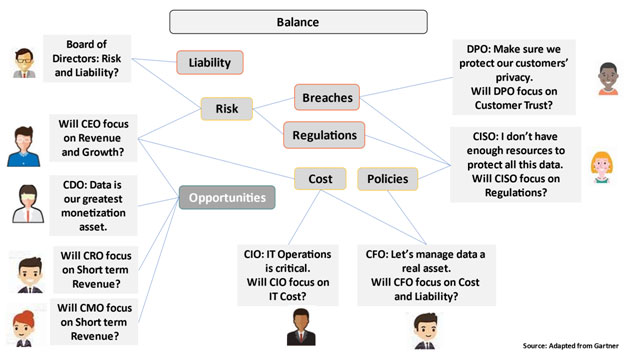
Risk Management and Solutions
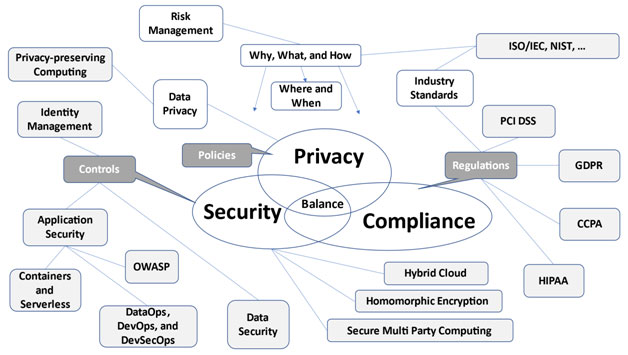
We discussed Frameworks for risk management and software development from NIST and other organizations earlier in this book. We also discussed security threats, privacy regulations, implementation aspects, and best practices:
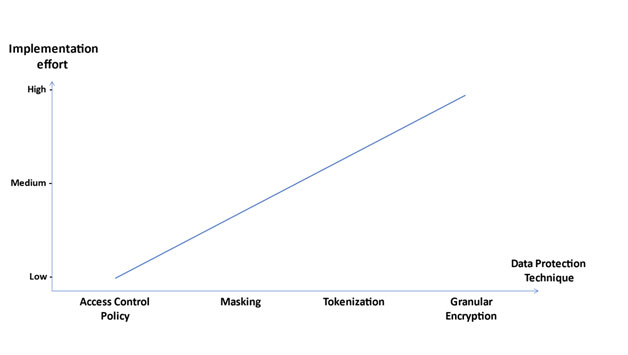
Start small with easy Data Protection techniques
One implementation approach is to start small with easy Data Protection techniques for the most urgent use cases and data in your organization:
Continuous Data discovery can find your evolving data assets across different environments.
Protection that balances different needs
Continue the implementation with granular Data Protection techniques for the most sensitive data in your organization.
Your data will be protected in a way the provides a balance between different requirements of the organization.
Protect the flow of data
Your data will be protected before it flows into cloud and mobile, and other distributed environments:
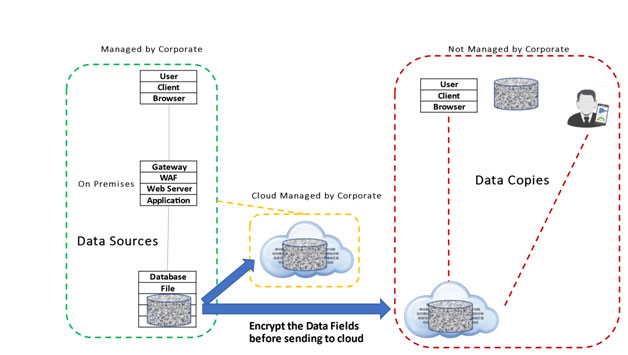
Your sensitive data will be protected from attacks when it flows and landeded in different environments.
Finding the Right Data Protection Solution
Finding the Right Data Protection for different use cases and data in your organization requires a good understanding of the problem that you want to solve:

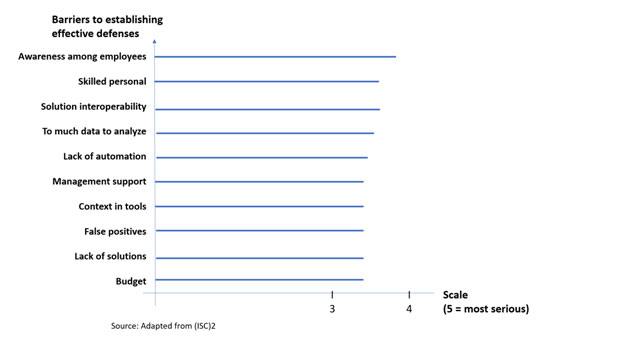
Barriers to Establishing Effective Defenses
Why are we not more secure? We have the tools, and budget is not a top issue. Still, awareness among employees and lack of skills are the top barriers to establishing effective defenses, according to a study by (ISC)2 in 2021:
Healthcare data breach costs increased
The healthcare sector keeps very sensitive and private information. Is that data adequately protected?
According to “Healthcare Organizations Are the Top Target for Ransomware Attackers,” the healthcare sector was the most targeted vertical for ransomware in 2020. Ransomware attacks seen in the first half of 2021 show a 102 percent increase from 2020’s numbers according to “Ransomware Keeps Healthcare in Crosshairs.” Healthcare data breach costs increased from an average total cost of $7.13 million in 2020 to $9.23 million in 2021, a 29.5% increase. More investments in Healthcare data protection can hopefully lower the loss of sensitive data.
In many cases, the attack’s goal isn’t just to encrypt data. According to “Detect, Protect, Recover: How Modern Backup Applications Can Protect You From Ransomware.”
The cost of a data breach is a 10% rise
The cost of a data breach in 2021 is US$ 4.24 million. This is a 10% rise from the average cost in 2019, which was $3.86 million according to “What is the Cost of a Data Breach in 2021?”. The $180 per record cost of a personally identifiable information breach is higher than payment card data.
Awareness training may not be enough
The attacker only needs to be successful once, but the defenders need to be successful 100% of the time to prevent breaches. This may require technology that can implement multi-layered security.
The Cost of Doing Business
There is a Cost of Doing Business. We need to find the right balance for our business between the cost of fraud and the cost of data security. For example, the card brands balance easy consumer experience with the cost of security solutions and payment fraud. Shoplifting and organized retail crime may be a bigger problem than computer fraud. PCI DSS helped in find in a baseline for an acceptable data security posture. Impactful enforcement encouraged larger retailers to be compliant.
More impactful enforcement may encourage organizations to comply to the letter and intent of GDPR in and HIPAA for healthcare in US and create a better security posture for PII and PHI (Protected Health Information.)
Data Leaks by Security Spending
The number of Data Leaks compared to Security Spending Budget. Manufacturing, retail, technology (software and internet services), and healthcare are in the upper part:
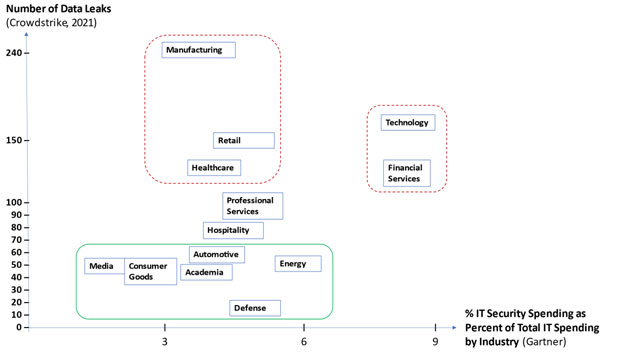
Is there a correlation between the Number of Breaches, data leaks, and Security Spending Budget?
Notes
- What is the Cost of a Data Breach in 2021? | UpGuard. https://www.upguard.com/blog/cost-of-data-breach
- Healthcare Organizations Are the Top Target for Ransomware Attackers, https://www.paloaltonetworks.com/blog/2021/08/healthcare-organizations-are-the-top-target/
- Highlights from the 2021 Unit 42 Ransomware Threat Report, https://unit42.paloaltonetworks.com/ransomware-threat-report-highlights/
- Ransomware Keeps Healthcare in Crosshairs. https://healthitsecurity.com/news/ransomware-attacks-surge-102-in-2021-as-triple-extortion-emerges
- Detect, Protect, Recover: How Modern Backup Applications Can Protect You From Ransomware,https://www.gartner.com/doc/reprints?id=1-258HHK51&ct=210217&st=sb
- INTERNATIONAL STANDARD ISO/IEC 20889, https://webstore.ansi.org/Standards/ISO/ISOIEC208892018?gclid=EAIaIQobChMIvI-k3sXd5gIVw56zCh0Y0QeeEAAYASAAEgLVKfD_BwE
- The real promise of synthetic data, https://news.mit.edu/2020/real-promise-synthetic-data-1016
- GDPR and protecting data privacy with cryptographic pseudonyms, https://www.ibm.com/blogs/insights-on-business/gbs-strategy/gdpr-protecting-data-privacy-cryptographic-pseudonyms/
- Synthetic data, https://en.wikipedia.org/wiki/Synthetic_data
- “Synthetic data”. McGraw-Hill Dictionary of Scientific and Technical Terms, The real promise of synthetic datahttps://news.mit.edu/2020/real-promise-synthetic-data-1016
- Data De-identification: Possibilities, Progress, and Perils, https://forge.duke.edu/blog/data-de-identification-possibilities-progress-and-perils
- The Privacy Myth of De-Identified Medical Data, https://medium.com/healthwizz/the-privacy-myth-of-de-identified-medical-data-10b9678e4bea












